How does it work?
How do I use it?
Security
How does it work?
Internet Sync allows two or more computers to collaborate on an incident, as long as both have a connection to the internet and have been given permission to acccess the incident.
Once you start or join an sync, any changes made to the incident on your computer are immediately transmitted to a central database. Every few seconds, your computer will query that central server, and look for new updates to the incident you're working on. If new updates are found, they'll be downlodaed an integrated into what you're doing.
In practical terms, it means a computer back at your training or deployment centre could be used to start generating IAP data while the crew is driving out to the field. Once you arrive, you can connect to the sync and see that information. Meanwhile, as planning checks people into the incident, logistics will see that data immediately.
How do I use it?
Start an internet sync
The first step in the process is to begin an internet sync. Use any computer that has the current incident information on it.
- Open the software and load the current incident if it isn't already
- Click on Network > Internet Sharing / Sync
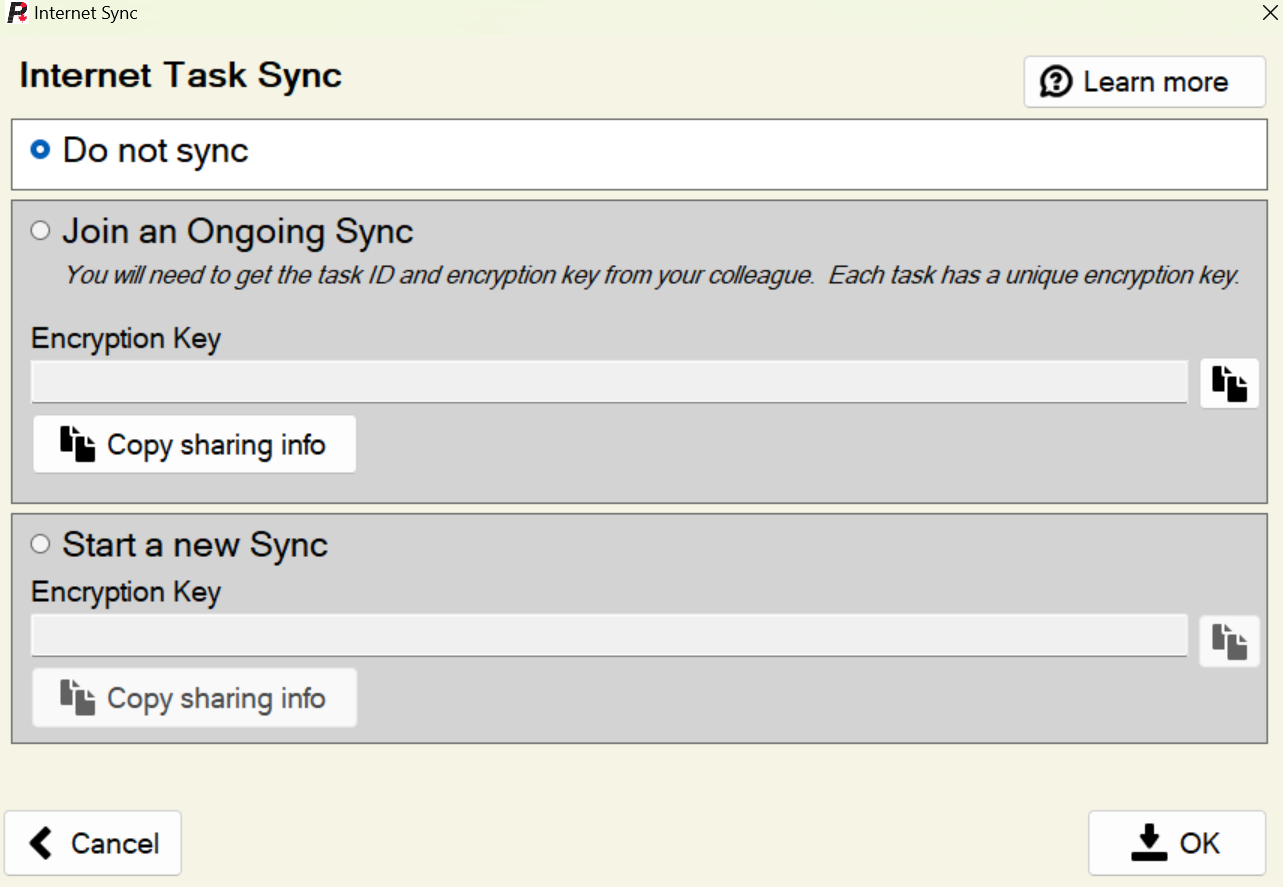
- You will now see a new screen with three options: Do not sync, Join an ongoing sync, and Start a new sync. Choose "Start a new Sync".
- The screen will display a randomly generated encryption key for you. Copy this key, using either of the buttons provided.
- Press "OK" and wait a few moments while the incident to date is uploaded to the internet server.
- Provide the encryption key you copied earlier to anyone else you want to join the incident.
Join an internet sync
Once a incident has been uploaded to the server, anyone else in possession of the encryption key is able to join the incident. You can also use this option if you have previously initiated a sync from this computer, but closed the program and are now re-opening it.
- Open the software if it isn't already. If you have a local copy of the incident, feel free to load that as well, it will speed up processing.
- Click on Network > Internet Sharing / Sync
- You will now see a new screen with three options: Do not sync, Join an ongoing sync, and Start a new sync. Choose "Join an Ongoing Sync".
- Enter the encryption key you've been provided by whoever set up the sync. If you are loading a file that was already synced, the information should be filled in for you.
- Press "OK" and wait a few moments while the incident to date is synchronized the internet server.
How is the information stored?
All incident information is stored in a central database on Microsoft's Azure cloud, located in Canada. Access to the server is restricted to key CIFFC employees.
The data is encrypted with 256-bit encryption on your device, then transmitted to the database encrypted where it is stored. Even the developers can't access the contents of your incident data (ie the server is blind to the data).
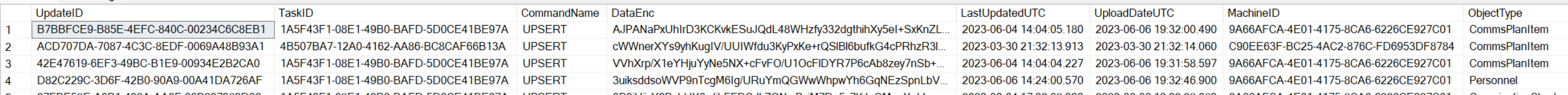
- UpdateID this is a randomly generated unique identifier for the individual update/change made to the incident. It is assigned on your computer, and serves only to identify that update among all other updates.
- TaskID this is a randomly generated unique identifier for the incident itself, and is common for all updates related to that specific incident. It is not related to the Task Number, Task Name, or any other identifiers. You may recognize it as the first half of your encryption key.
- CommandName this indicates the type of procedure being performed, either UPSERT to add or make changes, DELETE to remove something, or INITIAL for the initial incident information.
- DataEnc this is your encrypted data, containing the item being updated. Again, it is not readable on the server, or anywhere else, without your private encryption key.
- MachineID when the software is first installed on a computer, a unique identifier is randonly generated for that machine, internal to the software. This is used to identify the source of an update. There is no reference on the server of who this machine ID corresponds to, that information is only available on the computer itself.
- ObjectType this identifies the type of item being added/updated/deleted
Summary: What would be learned from the server?
Without the encryption key, someone could tell that an element of a comms plan was updated at 14:04 on the 4th of June, 2023 on the same incident, and by the same computer that updated the personnel at 14:24. There is no way to determine (a) which incident number or (b) which user/group or (c) the contents of the update.
If your IT department has additional questions or concerns please contact us.